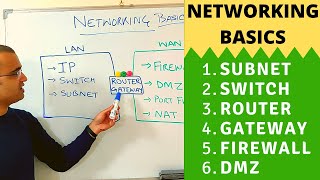
Published On Dec 23, 2020
You’ve probably heard about the latest major cyber attack, hitting organizations through a malicious code injection in a SolarWinds product. There’s a lot to it. Thankfully, CBT Nuggets trainer Keith Barker (@KeithBarker) is here to break down some of the details -- how it happened, how the perpetrators did it, and what can be done to prevent incidents like this from happening again.
Check out a detailed explanation of the SolarWinds Advanced Persistent Threat (APT) attack and other intrusion tactics on our blog: https://blog.cbt.gg/t9p
Not a CBT Nuggets subscriber? Start your free week: https://cbt.gg/2I5NxY1
-----------------
FireEye, one of the world’s leading cybersecurity firms, announced on December 8th, 2020, that state-sponsored hackers had broken into their systems and stole their penetration testing tools. This was the first discovery of the sweeping cyberattack, on malware they call “SUNBURST.” FireEye also discovered that they weren’t alone -- SolarWinds’ Orion update servers had been corrupted and weaponized by the very same hackers, affecting 18,000+ private and government organizations, going back to Spring of 2020.
At this point, no one can be certain how many customers this has affected, but this was easily one of the biggest cyberattacks of the decade. This massive breach impacts critical U.S. government agencies, including the Departments of State, Homeland Security, Energy, Treasury, Commerce, the Pentagon, and the National Institutes of Health.
International technology companies in the private sector weren’t spared either, as Cisco, Intel, Nvidia, Belkin, and VMware were all targeted as well.
-----------------
Connect with CBT Nuggets for the latest in IT training:
Twitter - / cbtnuggets
Facebook - / cbtnuggets
Instagram - / cbtnuggets
LinkedIn - / cbt-nuggets
#solarwinds #cybersecurity #cyberattack