Published On Apr 7, 2024
In this video, we discuss data encryption as it is covered on the Information Systems and Controls ISC CPA Exam.
Start your free trial: https://farhatlectures.com/
Data encryption is a technique used to lower the chances of unauthorized access and loss of data by applying cryptographic principles, ensuring data is safeguarded throughout its lifecycle of collection, processing, and storage. In simpler terms, cryptography uses a specific method, or algorithm, to change readable data, known as plaintext, into a scrambled format, referred to as ciphertext. This transformation makes the data unreadable to anyone who doesn't have the correct key to reverse the process. The key, when used with the algorithm, decodes the ciphertext back into plaintext. This process not only protects the data from being understood by unintended recipients but also provides a form of verification, known as nonrepudiation. Nonrepudiation is a security assurance that confirms the sender of the data is indeed who they claim to be, adding an extra layer of trust and security to the data exchange process.
Encryption techniques vary in how they use keys to secure data, and a single encryption approach can incorporate several key types. Organizations often employ encryption as an additional layer of security for data that is not actively being used or "at-rest," especially when their risk assessments indicate it's a necessary precaution.
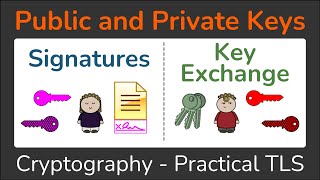
There are two main kinds of keys in encryption: public and private. Public keys are distributed widely or within specific groups, allowing anyone with the key to encrypt data intended for the key's owner. However, only the recipient, who possesses the corresponding private key, can decrypt this data. Private keys, on the other hand, are kept secret by a single user. This distinction forms the basis of secure data exchange, ensuring that information can be safely sent and received by verifying parties' identities through their unique key pairs.
Symmetric encryption is a method where a single key is used for both encoding and decoding data among a group of users. This key, which could be a number, a letter, or a mix of random characters, is known to everyone within the group. This approach is favored for situations requiring swift encryption and decryption, such as banking transactions involving sensitive customer information, where the process needs to be as quick as the transaction itself.
However, symmetric encryption has its limitations. Since the same key is used for both encryption and decryption by anyone who has it, it's impossible to prove who originally sent a message, lacking what is known as non-repudiation. This means you can't guarantee the identity of the person sending or receiving the encrypted information. Scaling this encryption method is challenging as well; every time a new member joins or leaves the group, new keys must be distributed among members to maintain security, making it cumbersome for larger groups.
For example, imagine a small business that uses a single password (the symmetric key) for all employees to access and edit a shared document containing sensitive information. While this method allows quick and easy access for authorized users, it also means any one of them could alter the document, and there would be no way to identify who made a change. If a new employee joins or an existing one leaves, the password would need to be changed and redistributed to ensure the document remains secure, illustrating the scalability issue.
#cpaexaminindia
#cpaexam #cpareviewcourse